Data Monitoring
Keeping track of your team is tough enough, but what about the flow of your data?
Data Monitoring & Sensing
XQ fulfills Zero Trust Data Monitoring & Sensing requirements within a data governance framework by leveraging several key capabilities that align with modern data security and governance standards. Here's how XQ addresses these aspects:
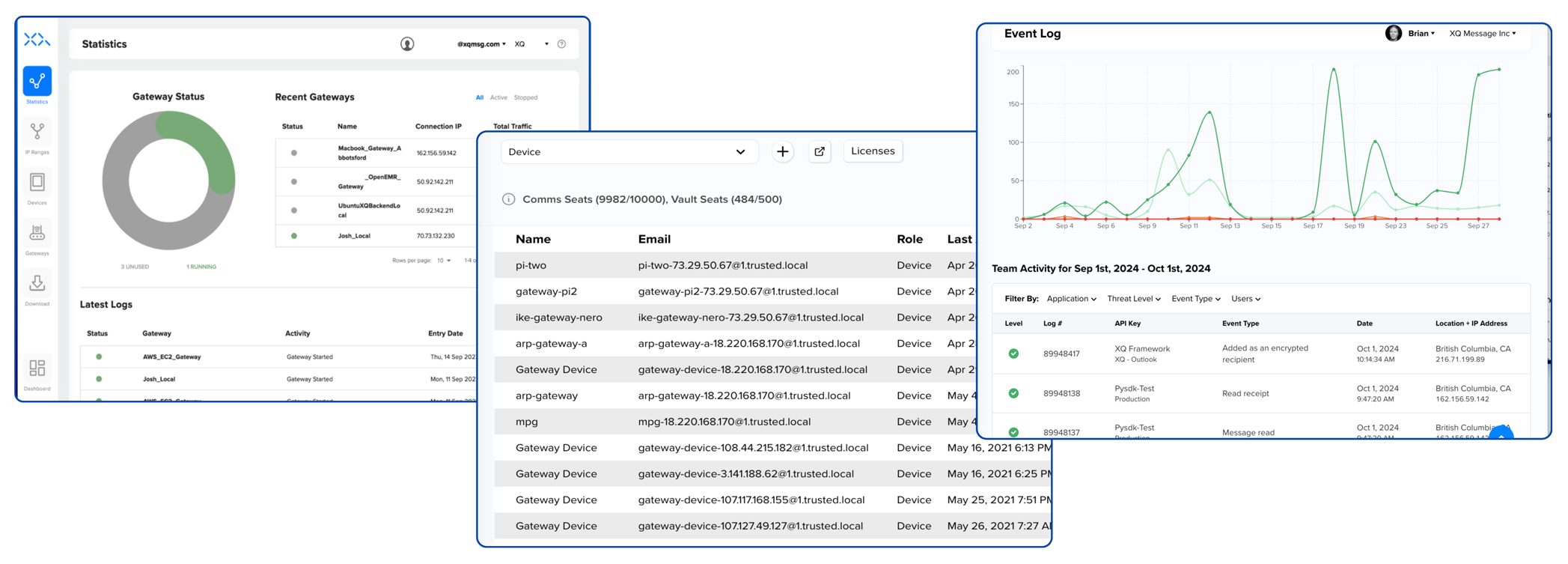
XQ acts as a data leash giving you control over your data everywhere it goes. All the events that are tied to each data object are recorded in the dashboard.
Zero Trust Data Monitoring & Sensing in Transit and at Rest
Granular Data Access Monitoring
XQ’s platform monitors real-time data access, when, and where. This visibility enables organizations to track data usage at a granular level.
Encrypted Data Flows with Real-Time Auditing
XQ secures data in motion with end-to-end encryption, ensuring that data is protected even as it traverses potentially insecure networks.
Automated Anomaly Detection & Response
By utilizing Agent-driven analytics, XQ’s platform can detect patterns of behavior that deviate from established norms.
Dynamic Policy Enforcement
Through its Zero Trust architecture, XQ enables dynamic enforcement of policies that control data access based on various contextual factors such as user identity, location, device security posture, and network conditions. This dynamic approach to policy enforcement ensures that access to sensitive data is continuously reevaluated, with actions taken to block or revoke access as needed.
Comprehensive Audit Trails for Compliance
XQ generates detailed audit trails for all data interactions. These logs provide crucial evidence for compliance with regulations such as GDPR, FISMA, CISA and HIPAA, by documenting all data access events, encryption actions, and policy changes. This level of transparency ensures organizations can meet governance requirements while adhering to a Zero Trust architecture.